VPN: All You Need to Know About VPNs, What They Do and How to Use Them
In this article, we'll detail everything you need to know about VPNs, what they do and how to use them. Click the link to read full guide..
Author:Daniel BarrettAug 19, 202231K Shares596.3K Views
Usually, we hear people say “VPN” but what does VPN mean, what does it do, and what does it entail? Proceed further with this article to find out more about VPNs and how they could be of efficient use to you.
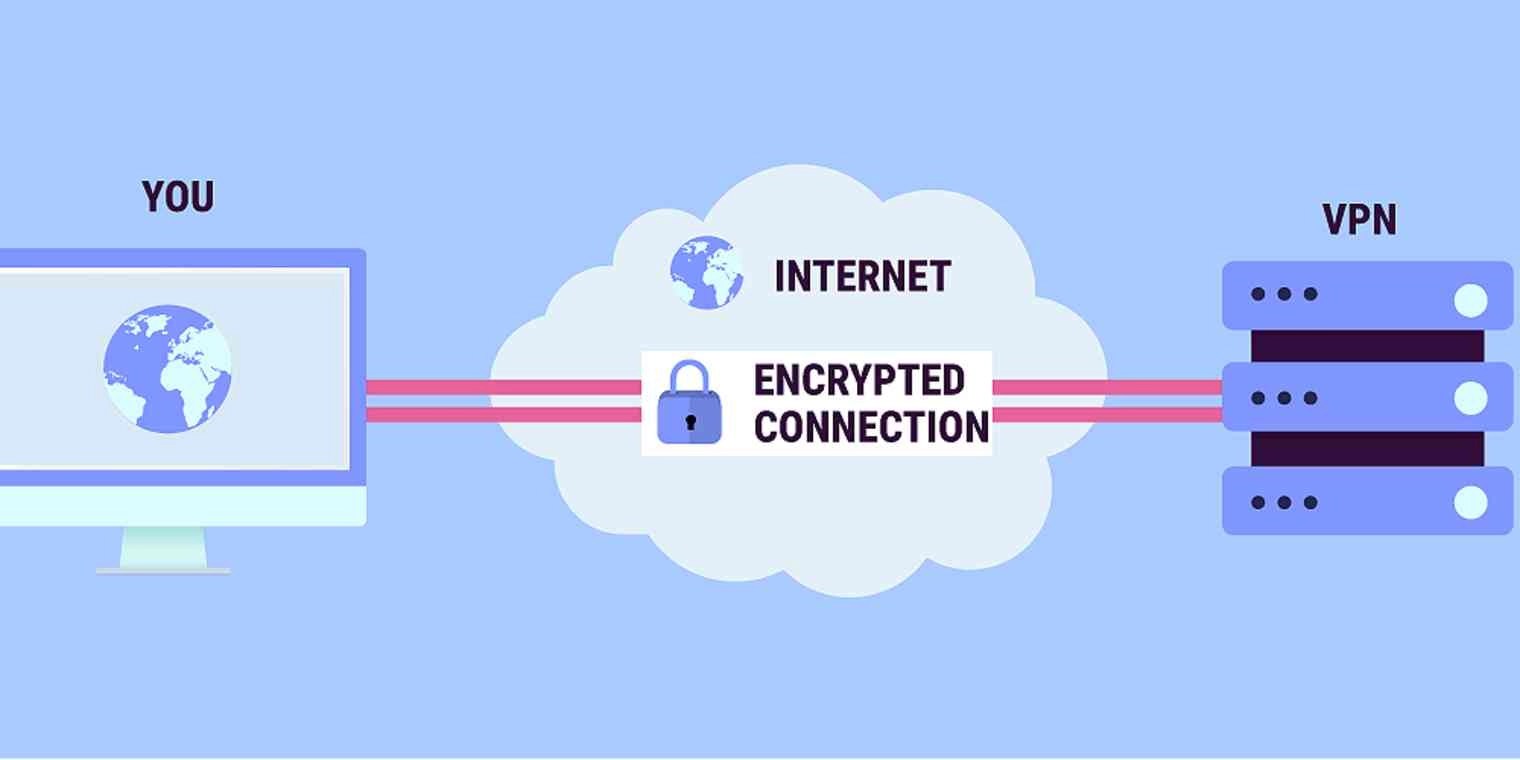
A VPN, or Virtual Private Network, allows you to create a secure connection to another network over the Internet. VPNs can be used to access region-restricted websites, shield your browsing activity from prying eyes on public Wi-Fi, and more.
These days Virtual Private Networks are really popular, but not for the reasons they were created. In the beginning, they were just a way to connect business networks securely over the internet or allow you to access a business network from home.
VPNs essentially forward all your network traffic to the network, which is where the benefits — like accessing local network resources remotely and bypassing Internet censorship — all come from. Most operating systems have integrated Virtual Private Network support.
How does a VPN work?
A VPN masks your IP address by letting the network redirect it through a specifically configured remote server run by a VPN host. This means that if you surf online with a Virtual Private Network, the VPN server becomes the source of your data. This means your Internet Service Provider (ISP) and other third parties cannot see which websites you visit or what data you send and receive online. A VPN works like a filter that turns all your data into “gibberish”. Even if someone were to get their hands on your data, it would be useless.
What Is a VPN and How Does It Help Me?
In very simple terms, a VPN connects your PC, smartphone, or tablet to another computer (called a server) somewhere on the internet, and allows you to browse the internet using that computer’s internet connection. So, if that server is in a different country, it will appear as if you are coming from that country, and you can potentially access things that you couldn’t normally.
So how does this help you? Good question! You can use a VPN to:
- Bypass geographic restrictions on websites or streaming audio and video.
- Watch streaming media like Netflix and Hulu.
- Protect yourself from snooping on untrustworthy Wi-Fi hotspots.
- Gain at least some anonymity online by hiding your true location.
- Protect yourself from being logged while torrenting.
Many people these days are using a VPN for torrenting or bypassing geographic restrictions to watch content in a different country. They are still very useful for protecting yourself while working at a coffee shop, but that’s hardly the only use anymore.
What are the benefits?
A VPN connection disguises your data traffic online and protects it from external access. Unencrypted data can be viewed by anyone who has network access and wants to see it. With a Virtual Private Network, hackers and cyber criminals can’t decipher this data.
- Access a Business Network While Traveling:Virtual Private Networks are frequently used by business travelers to access their business network, including all its local network resources, while on the road. The local resources don’t have to be exposed directly to the Internet, which increases security.
- Access Your Home Network While Travelling: You can also set up your VPN to access your network while traveling. This will allow you to access a Windows Remote Desktop over the Internet, use local file shares, and play games over the Internet as if you were on the same LAN (local area network).
Virtual Private Network
- Hide Your Browsing Activity FromYour Local Network and ISP: If you’re using a public Wi-Fi connection, your browsing activity on non-HTTPS websites is visible to everyone nearby, if they know how to look. If you want to hide your browsing activity for a bit more privacy, you can connect to a VPN. The local network will only see a single, secure VPN connection. All the other traffic will travel over the VPN connection. While this can be used to bypass connection monitoring by your Internet service provider, bear in mind that VPN providers may opt to log the traffic on their ends.
- Access Geo-Blocked Websites: Whether you’re an American trying to access your Netflix account while traveling out of the country or you wish you could use American media sites like Netflix, Pandora, and Hulu, you’ll be able to access these region-restricted services if you connect to a VPN located in the USA.
- Evade Internet Censorship: Many Chinese people use Virtual Private Networks to get around the Great Firewall of China and gain access to the entire Internet. (However, the Great Firewall has started interfering with VPNs recently.)
- Downloading Documents: Yes, let’s be honest — many people use Virtual Private Network connections to download files via BitTorrent. This can be useful even if you’re downloading completely legal torrents — if your ISP is throttling BitTorrent and making it extremely slow, you can use BitTorrent on a VPN to get faster speeds. The same is true for other types of traffic your ISP might interfere with (unless they interfere with VPN traffic itself.)
What are the disadvantages?
There aren’t too many disadvantages to using a VPN. But a possible one is that VPN could result in a slightly slower internet connection. That’s because a Virtual Private Network encrypts the data you send and receive, which could result in a lag while you browse the internet or download files.
Why should you use a VPN connection?
Your ISP usually sets up your connection when you connect to the internet. It tracks you via an IP address. Your network traffic is routed through your ISP’s servers, which can log and display everything you do online.
Your ISP may seem trustworthy, but it may share your browsing history with advertisers, the police or government, and/or other third parties. ISPs can also fall victim to attacks by cyber criminals: If they are hacked, your personal and private data can be compromised.
This is especially important if you regularly connect to public Wi-Fi networks. You never know who might be monitoring your internet traffic and what they might steal from you, including passwords, personal data, payment information, or even your entire identity.
Attributes of a functioning VPN
You should rely on your VPN to perform one or more tasks. The VPN itself should also be protected against compromise. These are the qualities you should expect from a comprehensive VPN solution:
- Encryption of your IP address: The primary job of a Virtual Private Network is to hide your IP address from your ISP and other third parties. This allows you to send and receive information online without the risk of anyone but you and the VPN provider seeing it.
- Encryption of protocols: A VPN should also prevent you from leaving traces, for example, in the form of your internet history, search history, and cookies. The encryption of cookies is especially important because it prevents third parties from gaining access to confidential information such as personal data, financial information and other content on websites.
- Kill switch: If your VPN connection is suddenly interrupted, your secure connection will also be interrupted. A good VPN can detect this sudden downtime and terminate preselected programs, reducing the likelihood that data is compromised.
- Two-factor authentication: By using a variety of authentication methods, a strong VPN checks everyone who tries to log in. For example, you might be prompted to enter a password, after which a code is sent to your mobile device. This makes it difficult for uninv
The history of Virtual Private Networks
Since humans have been using the internet, there has been a movement to protect and encrypt internet browser data. The US Department of Defense already got involved in projects working on the encryption of internet communication data back in the 1960s.Their efforts led to the creation of ARPANET (Advanced Research Projects Agency Network), a packet switching network, which in turn led to the development of the Transfer Control Protocol/Internet Protocol (TCP/IP).
The TCP/IP had four levels: Link, internet, transport, and application. At the internet level, local networks and devices could be connected to the universal network – and this is where the risk of exposure became clear. In 1993, a team from Columbia University and AT&T Bell Labs finally succeeded in creating a kind of the first version of the modern VPN, known as swIPe: Software IP encryption protocol.
In the following year, Wei Xu developed the IPSec network, an internet security protocol that authenticates and encrypts information packets shared online. And In 1996, a Microsoft employee named Gurdeep Singh-Pall created a Peer-to-Peer Tunneling Protocol (PPTP).
The First Virtual Private Networks
Contiguous to Singh-Pall developing PPTP, the internet was growing in popularity and the need for consumer-ready, sophisticated security systems emerged. At that time, anti-virus programs were already effective in preventing malware and spyware from infecting a computer system. However, people and companies also started demanding encryption software that could hide their browsing history on the internet.
The first VPNs, therefore, started in the early 2000s but were almost exclusively used by companies. However, after a flood of security breaches, especially in the early 2010s, the consumer market for VPNs started to pick up.
VPNs and their current use
According to GlobalWebIndex, the number of VPN users worldwide increased more than fourfold between 2016 and 2018. In countries such as Thailand, Indonesia, and China, where internet use is restricted and censored, one in five internet users uses a VPN. In the USA, Great Britain, and Germany, the proportion of VPN users is lower at around 5% but is budding.
One of the biggest drivers for VPN adoption in recent years has been the increasing demand for content with geographical access restrictions. For example, video streaming services such as Netflix or YouTube make certain videos available only in certain countries. With contemporary VPNs, you can encrypt your IP address so that you appear to be surfing from another country, enabling you to access this content from anywhere.
Here’s How to Browse Securely With a VPN
A VPN encrypts your surfing behavior, which can only be decoded with the help of a key. Only your computer and the Virtual Private Network know this key, so your ISP cannot recognize where you are surfing. Different VPNs use different encryption processes, but generally function in three steps:
- Once you are online, start your VPN. It acts as a secure tunnel between you and the internet. Your ISP and other third parties cannot detect this tunnel.
- Your device is now on the local network of the VPN, and your IP address can be changed to an IP address provided by the VPN server.
- You can now surf the internet at will, as the Virtual Private Network protects all your data.
What kind of VPNs are There?
There are many different types of VPNs, but you should be familiar with the three main types:
1. SSL Virtual Private Network
Often not all employees of a company have access to a company laptop they can use to work from home. During the corona crisis in Spring 2020, many companies faced the problem of not having enough equipment for their employees. In such cases, the use of a private device (PC, laptop, tablet, mobile phone) is often resorted to. In this case, companies fall back on an SSL-VPN solution, which is usually implemented via a corresponding hardwarebox.
The prerequisite is usually an HTML-5-capable browser, which is used to call up the company’s login page. HTML-5 capable browsers are available for virtually any operating system. Access is guarded with a username and password.
2. Site-to-site Virtual Private Network
A site-to-site VPN is essentially a private network designed to hide private intranets and allow users of these secure networks to access each other’s resources.
It’s also useful if you have multiple locations in your company, each with its local area network (LAN) connected to the WAN (Wide Area Network). Site-to-site Virtual Private Networks are also useful if you have two separate intranets between which you want to send files without users from one intranet explicitly accessing the other.
Site-to-site VPNs are mainly used in large companies. They are complex to implement and do not offer the same flexibility as SSL VPNs. However, they are the most effective way to ensure communication within and between large departments.
3. Client-to-Server Virtual Private Network
Connecting via a VPN client can be imagined as if you were connecting your home PC to the company with an extension cable. Employees can dial into the company network from their home office via the secure connection and act as if they were sitting in the office. However, a Virtual Private Network client must first be installed and configured on the computer.
This involves the user not being connected to the internet via his ISP, but establishing a direct connection through his/her VPN provider. This essentially shortens the tunnel phase of the VPN journey. Instead of using the Virtual Private Network to create an encryption tunnel to disguise the existing internet connection, it can automatically encrypt the data before it is made available to the user.
This is an increasingly common form of Virtual Private Network, which is particularly useful for providers of insecure public WLAN. It prevents third parties from accessing and compromising the network connection and encrypts data to the provider. It also prevents ISPs from accessing data that, for whatever reason, remains unencrypted and bypasses any restrictions on the user’s internet access (for instance, if the government of that country restricts internet access).
The advantage of this type of VPN access is greater efficiency and universal access to company resources. Provided an appropriate telephone system is available, the employee can, for example, connect to the system with a headset and act as if he/she were at their company workplace. For example, customers of the company cannot even tell whether the employee is at work in the company or their home office.
How do I Install a VPN on My Computer?
Before installing a VPN, it is important to be familiar with the different implementation methods:
1. VPN user
Software must be installed for standalone VPN clients. This software is configured to meet the requirements of the endpoint. When setting up the VPN, the endpoint executes the VPN link and connects to the other endpoint, creating the encryption tunnel. In companies, this step usually requires the entry of a password issued by the company or the installation of an appropriate certificate. By using a password or certificate, the firewall can recognize that this is an authorized connection. The employee then identifies him/herself using credentials known to him/her.
2. Browser extensions
VPN extensions can be added to most web browsers such as Google Chrome and Firefox. Some browsers, including Opera, even have their own integrated Virtual Private Network extensions. Extensions make it easier for users to quickly switch and configure their VPN while surfing the internet. However, the connection is only valid for information that is shared in this browser. Using other browsers and other internet uses outside the browser (e.g. online games) cannot be encrypted by the Virtual Private Network.
While browser extensions are not quite as comprehensive as VPN clients, they may be an appropriate option for occasional internet users who want an extra layer of internet security. However, they have proven to be more susceptible to breaches. Users are also advised to choose a reputable extension, as data harvesters may attempt to use fake VPN extensions. Data harvesting is the collection of personal data, such as what marketing strategists do to create a personal profile of you. Advertising content is then personally tailored to you.
3. Router VPN
If multiple devices are connected to the same internet connection, it may be easier to implement the VPN directly on the router than to install a separate VPN on each device. A router VPN is especially useful if you want to protect devices with an internet connection that are not easy to configure, such as smart TVs. They can even help you access geographically restricted content through your home entertainment systems.
A router Virtual Private Network is easy to install, always provides security and privacy, and prevents your network from being compromised when insecure devices log on. However, it may be more difficult to manage if your router does not have its user interface. This can lead to incoming connections being blocked.
4. Company VPN
A company VPN is a custom solution that requires personalized setup and technical support. The VPN is usually created for you by the company’s IT team. As a user, you have no administrative influence from the VPN itself, and your activities and data transfers are logged by your company. This allows the company to minimize the potential risk of data leakage. The main advantage of a corporate Virtual Private Network is a fully secure connection to the company’s intranet and server, even for employees who work outside the company using their internet connection.
Are VPNs Available on Smartphones?
Yes, there are several VPN options for smartphonesand other internet-connected devices. A VPN can be essential for your mobile device if you use it to store payment information or other personal data or even just to surf the internet. Many VPN providers also offer mobile solutions – many of which can be downloaded directly from Google Play or the Apple App Store, such as Kaspersky VPN Secure Connection.
Is a VPN so Secure?
It is important to note that VPNs do not function like comprehensive anti-virus software. While they protect your IP and encrypt your internet history, a VPN connection does not protect your computer from outside intrusion. To do this, you should use anti-virus software such as Kaspersky Internet Security. Because using a VPN on its own does not protect you from Trojans, viruses, bots, or other malware.
Once the malware has found its way onto your device, it can steal or damage your data, whether you are running a VPN or not. It is therefore important that you use a VPN together with a comprehensive anti-virus program to ensure maximum security.
Choosing a Secure Virtual Private Network Provider
It is also important that you choose a VPN provider that you can trust. While your ISP cannot see your internet traffic, your VPN provider can. If your Virtual Private Network provider is compromised, so are you. For this reason, you must choose a trusted VPN provider to ensure both the concealment of your internet activities and ensure the highest level of security.
Installing a VPN Connection on Your Smartphone
As previously stated, there are also VPN connections for Androidsmartphones and iPhones. Fortunately, smartphone VPN services are easy to use and generally include the following:
The installation process usually only downloads one app from the iOS App Store or Google Play Store. Although free VPN providers exist, it’s wise to choose a professional provider when it comes to security.
- The setup is extremely user-friendly, as the default settings are already mostly designed for the average smartphone user. Simply log in with your account. Most apps will then guide you through the key functions of the VPN services.
- Switching on the VPN works like a light switch for many VPN apps. You will probably find the option directly on the home screen.
- Server switching is usually done manually if you want to fake your location. Simply select the desired country from the offer.
- Advanced setup is available for users requiring a higher degree of data protection. Depending on your VPN, you can also select other protocols for your encryption method. Diagnostics and other functions may also be available in your app. Before you subscribe, learn about these features to find the right VPN for your needs.
- To surf the internet safely from now on, all you have to do is first activate the VPN connection through the app.
- But keep the following in mind: A VPN is only as secure as the data usage and storage policies of its provider.
Virtual Private Network
Remember that the VPN service transfers your data to their servers and these servers connect over the internet on your behalf. If they store data logs, make sure that it is clear for what purpose these logs are stored. Serious VPN providers usually put your privacy first and foremost. You should therefore choose a trusted provider such as Kaspersky Secure Connection.
Remember that only internet data is encrypted. Anything that does not use a cellular or Wi-Fi connection will not be transmitted over the internet. As a result, your VPN will not encrypt your standard voice calls or texts.
Is a VPN Authorized?
VPNs are not illegal in the United States. However, not all countries have the same laws regarding these services. For instance, China, Russia, and North Korea either regulate or ban VPNs. You should know, too, that if you commit an illegal act online using a VPN, that act is still illegal. Customers often use VPNs so that they can stream sporting events and TV shows that they may be blocked from accessing in their region. Using a VPN to pretend that you are logging onto the internet from a different location might violate the service agreements of streaming services.
Are free Virtual Private Networks Safe?
You can choose from many free VPNs. This could be useful if you are on a limited budget. Be aware, though, that free VPN services might not provide the same type of browsing privacy that pay services offer. Free Virtual Private Networks have to make money somehow. They might do this by tracking and collecting your browsing data and selling it to third parties, like advertisers. Others might hit you with a steady stream of online ads. It might be easier on your wallet, but using one might compromise some of your privacy.
Can You be Tracked if You Use a VPN
Your VPN provider should both encrypt the data you send and receive your data and hide your IP address. This means that criminals, hackers, and others won’t be able to track your online activities. However, your internet service provider — also known as your ISP — can determine if you are using a VPN by looking at your IP address. If it doesn’t match, your provider will know that you are using a Virtual Private Network when connecting to the internet. Fortunately, your internet service provider still won’t be able to track your browsing activity if you are using a VPN.
Using a VPN for its Maximum Protection
If you want the most protection, you should leave your VPN on at all times. You should especially leave your VPN on when you are logging onto the internet using public Wi-Fi. These connections are notoriously insecure, providing tempting targets for hackers and cybercriminals. You should also use a VPN whenever you are logging into your credit card or online banking accounts. You don’t want to expose this sensitive financial information to online thieves.
Does Your VPN Drain Battery?
A VPN will consume more of your battery’s power when it is on. This can be a problem when you are using a VPN with your smartphone. Many Virtual Private Networks do come with a “power saver” feature, though. This automatically turns your VPN off when your device’s screen turns off. Then, when you turn your device back on, the VPN automatically turns itself back on, too.
Is using a VPN Safe For Banking?
Because a VPN encrypts the data you send, such as when you enter your log-in credentials, it can protect you while you are visiting your bank’s online portal. Snoops won’t be able to see your log-in information if you first connect to a Virtual Private Network. This is especially helpful if you must access your online bank through a public Wi-Fi connection. You should only do this in an emergency because such online connections are so vulnerable to hackers. But by logging onto public Wi-Fi through a VPN, you can block your browsing activity from cybercriminals, hackers, and other spies.
Summary
A VPN connection establishes a secure connection between you and the internet. Via the Virtual Private Network, all your data traffic is routed through an encrypted virtual tunnel. This disguises your IP address when you use the internet, making its location invisible to everyone. A VPN connection is also secure against external attacks. That’s because only you can access the data in the encrypted tunnel – and nobody else can because they don’t have the key. A Virtual Private Network allows you to access regionally restricted content from anywhere in the world.
Many streaming platforms are not available in every country. You can still access them using the VPN. Virtual Private Network solutions from Kaspersky are available for both Windows PCs and Apple Macs.
There are a variety of providers of VPN connections for smartphones that keep mobile data traffic anonymous. You can get certified providers in the Google Play Store or the iOS App Store. However, do not forget that only your data traffic on the internet is anonymized and protected by using a VPN. The VPN connection does not protect you from hacker attacks, Trojans, viruses or other malware. You should therefore have additional trusted anti-virus software.
Editor’s picks:
Jump to
How does a VPN work?
What Is a VPN and How Does It Help Me?
What are the benefits?
What are the disadvantages?
Why should you use a VPN connection?
Attributes of a functioning VPN
The history of Virtual Private Networks
The First Virtual Private Networks
VPNs and their current use
Here’s How to Browse Securely With a VPN
What kind of VPNs are There?
1. SSL Virtual Private Network
2. Site-to-site Virtual Private Network
3. Client-to-Server Virtual Private Network
How do I Install a VPN on My Computer?
1. VPN user
2. Browser extensions
3. Router VPN
4. Company VPN
Are VPNs Available on Smartphones?
Is a VPN so Secure?
Choosing a Secure Virtual Private Network Provider
Installing a VPN Connection on Your Smartphone
Is a VPN Authorized?
Are free Virtual Private Networks Safe?
Can You be Tracked if You Use a VPN
Using a VPN for its Maximum Protection
Does Your VPN Drain Battery?
Is using a VPN Safe For Banking?
Summary

Daniel Barrett
Author
Daniel Barrett is a tech writer focusing on IoT, gadgets, software, and cryptocurrencies. With a keen interest in emerging technologies, Daniel offers expert analysis and commentary on industry trends. Follow him for authoritative insights into the latest tech innovations.
Latest Articles
Popular Articles